As seen in the South Florida Business Journal
The advancement and usage of technologies have made it easier for bad actors (black hats) to cause damage to business enterprises and individuals at a much larger scale. Twenty years ago, the most advanced hackers were utilizing techniques such as penny-shaving schemes to misappropriate cash from their victims.
The IBM Security 2022 Cost of Data Breach report presented the following key findings:
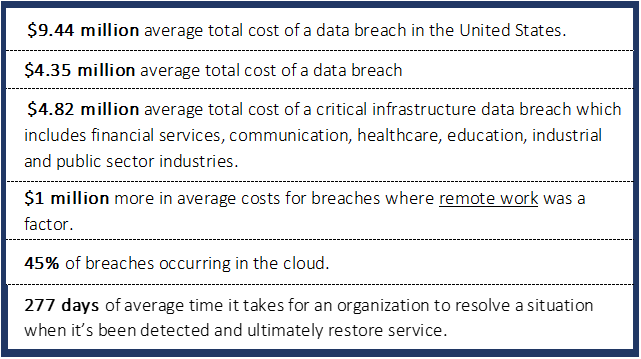
These statistics should be alarming to anyone, particularly as costs and remote working conditions continue to increase. The cause of losses may come in a variety of forms which include ransomware, hacking, business email compromises (BEC), phishing or malicious insiders. Losses may occur from misappropriation, ransom, trademark/copyright infringement and incident response/recovery costs.
Strong controls and proactive strategies to mitigate risk will generate a higher long-term return on investment. Cyber professionals constantly emphasize that the threat is a matter of when, not if it will happen or not. The remote working environment increases the susceptibility to attack, and results in a higher appetite for hackers to engage.
Some approaches for businesses to utilize when considering the existence and mitigation of threats include:
- Employee and stakeholder training: This includes the adoption of a strong security culture and policy and extends beyond the internal organization structure. Per the IBM Security 2022 report, “19% of breaches occurred because of a compromise at a business partner.”
- Systems assessment and upgrading: Complete a cybersecurity risk assessment to identify where risks are most likely to occur and then develop a remediation plan to address them. This assessment should be supplemented with vulnerability management procedures to test the perimeter protections and internal network monitoring of your technology environment. Based on the findings of this exercise, any systems that result in a potential weakness that can be leveraged by intruders should be fortified or replaced with updated tools to enable a successful defense strategy.
- Business continuity plan and incident response (IR): By preparing for an incident, a business’s ability to respond and recover from a cyberattack will be exponentially improved. Identify internal and external resources that will be responsible for mitigating the damage and restoring operations. These professionals may include cybersecurity specialists, systems engineers, legal counsel, insurance providers and forensic accountants.
- Cyber insurance: This was once an unfamiliar territory for insurance carriers, but current predictions of the size of the global insurance market suggest rapid growth will occur over the next five years. Cyber insurance will provide coverage to businesses and individuals to recover losses and expenses resulting from cyber incidents. Business interruption coverage is offered in cyber insurance policies, which is intended to reimburse businesses for lost income from such events.
It is becoming more common for businesses to engage forensic accountants (FAs) to assist in the planning and risk mitigation process. They can assist businesses with identifying assets at risk, estimating the potential cost, and building the internal control process.
When an incident occurs, a business may find themselves in unfamiliar territory resulting from litigation or bottom-line losses. The IR should be swift and strategic. FAs may play a significant role in expediting this process by assisting the IR team to investigate, quantify and report on financial implications. FAs may work in conjunction with the affected business, insurance carriers or litigation teams.
The form of losses/damages and the affected stakeholders will vary from case to case. However, the FA will be integral in both restoring the business and stakeholders position pre-incident. The effort includes the review of financial statements, budgets, internal controls, interviewing internal parties, interviewing external parties, forecasting and reporting the information. Like other cyber specialists, FAs will need to present their findings and conclusions in a form that allows stakeholders and executives to make informed decisions. In some cases, FAs will assist in resolving differences between parties in matters such as insurance coverage and litigation.
Businesses may also encounter situations where resolutions of value are required to compensate customers for personal records intended to be maintained in confidentiality, such as email addresses, social security numbers, credit card information and financial records.
It’s reasonable to assume the job of an FA would be straightforward when tracing misappropriated cash from a penny-shaving scheme. However, recovering the misappropriated assets from the cyber-assailants can be a more challenging process. The process could involve litigation to recover damages or attempting to recover assets in bankruptcy court.
For more information on how Citrin Cooperman can support your business, contact Nicholas Landera at nlandera@citrincooperman.com.
